Cross-Origin Resource Sharing (CORS) Misconfiguration leads to User’s PII leaks.
Hello everyone,
I’m Tarikul Islam, a Cyber Security Researcher from Sec Miner’s Bangladesh.
Now I am telling you a story of CORS Vulnerability.
* Detection
* Initial Exploit
* Mistake
* Final Exploit
I picked a site as a new target to check security issues and went to wappalyzer to check the site. The site was under Cloudflare protection.

After a minute of silence, I start collecting subdomains. Fire the Burp Suite, create an account, and surface on the web pages.
After checking some different endpoints, I checked the Burp Suite history. I realized the site was under a session base API server.

I saw in the response like this.
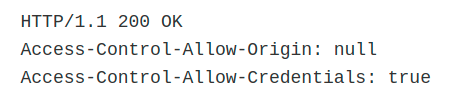
Let’s try CORS now 😃
When I tested it on my local machine, it worked fine. I upload it on VPS. It won’t work because I used the FILE protocol in my local machine but on VPS using the HTTP protocol.

Thirty minutes I was testing various methods to bypass protocol. Shut down the computer, leaning on my bed. Suddenly, I remembered a year ago; I faced the same problem at Port Swigger Academy.
They have an exploit for a null origin value.
Uploaded this exploit on VPS. Exploit worked this time successfully.
